The Justice Department has announced the unsealing of two warrants authorising the seizure of five internet domains used by malicious cyber actors to operate the LummaC2 information-stealing malware service.
“The Department will continue to use its unique tools, authorities, and partnerships to disrupt malicious cyber operations and criminal networks,” said Sue J. Bai, head of the Justice Department’s National Security Division.
Bai added, “Today’s disruption is another instance where our prosecutors, agents, and private sector partners came together to protect us from the persistent cybersecurity threats targeting our country. We are grateful for their work and dedication.”
Malware like LummaC2 is deployed to steal sensitive information such as user login credentials from millions of victims in order to facilitate a host of crimes, including fraudulent bank transfers and cryptocurrency theft, said Matthew R. Galeotti, head of the Justice Department’s Criminal Division.
He noted that Wednesday’s announcement “demonstrates that the Justice Department is resolved to use court-ordered disruptions like this one to protect the public from the theft of their personal information and their assets”.
Galeotti reiterated the Justice Department’s commitment to working with and “appreciates the efforts of the private sector to safeguard the public from cybercrime”.
As alleged in the affidavits filed in support of the government’s seizure warrants, the administrators of LummaC2 used the seized websites to distribute LummaC2, an information-stealing malware, to their affiliates and other cyber criminals.
According to court documents, common targets for cybercriminals using malware like LummaC2 include browser data, autofill information, login credentials for accessing email and banking services, as well as cryptocurrency seed phrases, which permit access to virtual currency wallets.
As alleged in the affidavits, the FBI has identified at least 1.7 million instances where LummaC2 was used to steal this type of information.
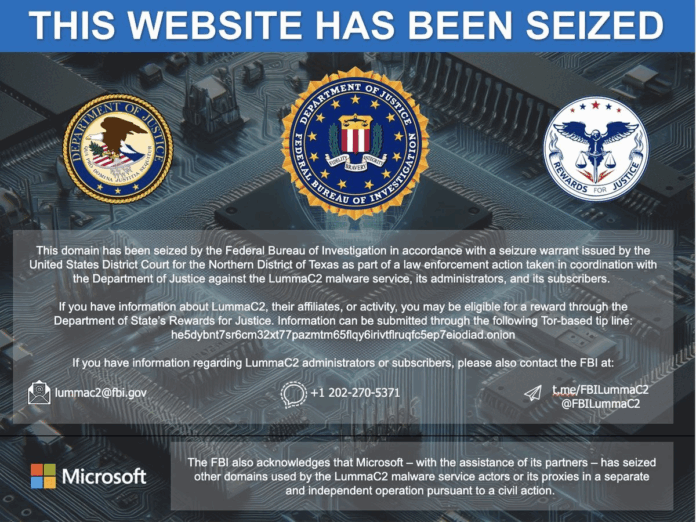
The government’s affidavit further alleges that the seized domains, also referred to as user panels, served as login pages for the LummaC2 malware, allowing credentialed users and administrators to access and deploy LummaC2.
On May 19, 2025, the government seized two domains. On May 20, 2025, as detailed in court documents, the LummaC2 administrators informed their users of three new domains that they had set up to host the user panel. The next day, the government then seized those three domains.
The seizure of these domains by the government will prevent the owners and cybercriminals from using the websites to access LummaC2 to compromise computers and steal victim information.
Individuals who now visit the websites will see a message indicating that the site has been seized by the Justice Department, including the FBI.
Concurrent with Wednesday’s actions and consistent with the Justice Department’s approach to public-private operational coordination, Microsoft announced an independent civil action to take down 2,300 internet domains also claimed to be used by the LummaC2 actors or their proxies.




mrdbjt
As a newbie in this field, this article is very practical for me. I hope to continue to update it!
As a newbie in this field, this article is very practical for me. I hope to continue to update it!